In software development, DevOps is the combination of specific development activities with IT operations. This combination aims to improve software quality and enable continuous delivery. If we add security management to DevOps, it becomes DevSecOps: a discipline that integrates security as a shared responsibility between the IT world and the software development world. In the past, security was the exclusive responsibility of a specialized team that joined projects in their final phases. This worked well in development cycles that lasted months or years. But in agile development cycles measured in weeks, security practices must be considered from the beginning to the end of the project, and security responsibilities must be shared by the entire development and IT teams. For DevSecOps to work without breaking the paradigms of agile methodologies, its integration must be automated. This is the only way for the DevOps workflow not to become sluggish when incorporating security management. And that automation requires appropriate mechanisms that integrate development tools, such as integrated development environments (IDEs), with security features.
Types of DevSecOps Tools
The combination of security and DevOps can take many forms. For this reason, there are different types of DevSecOps tools, which can be summarised as follows:
Vulnerability scanning in open source components: They look for possible vulnerabilities in open source code components and libraries resident in the analyzed code base, along with all their dependencies. Static and dynamic application security testing (SAST/DAST): Static testing scans developers’ source code for insecure code to identify potential security issues. Dynamic testing performs security tests on running applications without requiring access to the source code. Image scanning: They search for vulnerabilities in Docker containers. Infrastructure automation: Detect and fix various configuration issues and vulnerabilities in infrastructure configuration, particularly in cloud environments. Visualization: Provide visibility into KPIs and trends to detect increases or decreases in the number of vulnerabilities over time. Threat modeling: Enable proactive decision-making by predicting threat risks across the entire attack surface. Alerts: Notify the security team only when an anomalous event has been identified and prioritized as a threat to reduce the noise level and avoid interruptions in DevSecOps workflows.
The list below shows a curated list of DevSecOps tools you can rely on to incorporate the word “Sec” into your DevOps workflows.
Invicti
Invicti is a tool that you can integrate into your SDLC to carry out security management in your software products while maintaining the agility of the development process. The analysis performed by Invicti is exhaustive, providing accuracy in detecting problems without sacrificing speed in the management of the SDLC. The automation options offered by Invicti avoid the need for human intervention in the execution of security tasks, creating effort savings for your team that can amount to hundreds of hours per month. These savings are enhanced by identifying the vulnerabilities that really matter and automatically assigning them to the most appropriate resources for remediation. Invicti also provides complete visibility into the vulnerabilities in your applications under development and the efforts being made to reduce risk.
SonarQube
SonarQube automatically checks your code for vulnerabilities, sniffing it for bugs that could become threats. At the time of this writing, it supports nearly 30 different programming languages. SonarQube’s unique QualityGates represent a simple way to stop issues before a product goes out into the world. They also provide the development team with a joint view of quality, allowing everyone to know the standards and whether their developments meet them. SonarQube integrates seamlessly into your DevSecOps pipeline, ensuring that all team members have access to the reports and feedback generated by the tool. By simply installing it, SonarQube clearly indicates if your commits are clean and if your projects are ready for release. If something is wrong, the tool will immediately inform you where the problem is and what the solution can be.
Aqua
Aqua allows you to visualize and stop threats at every stage of the lifecycle of your software products, from writing the source code to deploying the application in the cloud. Operating as a cloud-native application protection platform (CNAPP), the tool offers software supply chain security checks, risk and vulnerability scanning, and advanced malware protection. Aqua’s integration options allow you to secure your applications regardless of the platforms and mechanisms you use for development and deployment, whether they are cloud, container, serverless, CI/CD pipelines, or orchestrators. It also integrates with SIEM platforms and analytics tools. A distinctive aspect of Aqua is that it enables security control in Kubernetes containers with KSPM (Kubernetes Security Posture Management) and advanced protection in Kubernetes runtime. Using native K8s features enables policy-driven protection for the entire lifecycle of applications deployed in containers.
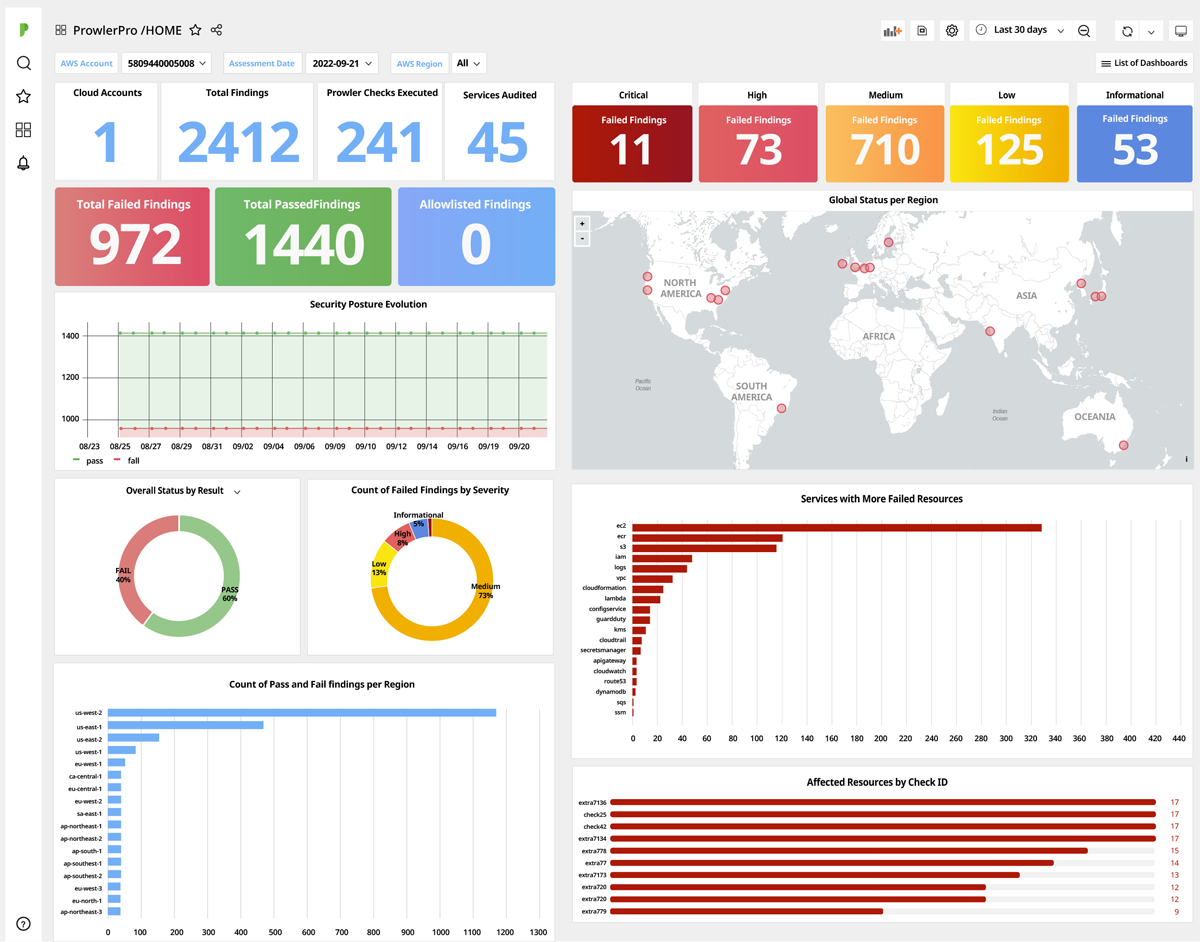
ProwlerPro
ProwlerPro is designed in such a way that you can create an account and start performing scans of your development pipelines in a matter of minutes, providing a holistic view of your infrastructure regardless of the region in which you are located. Its visualization tools allow you to view the security status of all your AWS services in a single window. Once you create your ProwlerPro account and get up and running, you can configure the system to run a series of recommended checks every 24 hours automatically. Scans with ProwlerPro run in parallel for speed so as not to slow with your DevSecOps workflows. Scan results are displayed in a series of predefined dashboards that can be easily shared and navigated by drilling down for direct insights at any level of detail of your security posture.
Probely
If you already have a DevOps workflow and are looking to integrate security scans into it, Probely allows you to do so in a matter of minutes, thanks to its web application vulnerability scanning tools and APIs. Probely’s approach is based on API-first development, which means that each new feature of the tool is first offered through the API and then added to the interface. This strategy makes it possible if you need to integrate Probely with workflows or custom software, you can always using its API. You can also register webhooks so that your applications receive notifications for each event that Probely generates. Since Probely offers a number of out-of-the-box integrations, chances are you won’t have to use its API to integrate it with your tools. If you already use Jira and Jenkins in your workflows, the integration will be instant. Probely will automatically initiate scans in your CI/CD pipelines and register the vulnerabilities found as issues in Jira. Once those vulnerabilities are resolved, it will test them again and reopen the unresolved issue in Jira, if necessary.
Checkov
Checkov scans configurations in cloud infrastructures with the intention of finding configuration flaws before deploying a software product. With a common command line interface, it scans results across diverse platforms, such as Kubernetes, Terraform, Helm, CloudFormation, ARM Templates, and Serverless frameworks. With an attribute-based policy scheme, Checkov allows you to scan cloud resources at compile time, detecting configuration errors in attributes using a simple policy-as-code Python framework. Among other things, Checkov analyzes relationships between cloud resources using graph-based YAML policies. By integrating into CI/CD pipelines and version control systems, Checkov executes, tests, and modifies runner parameters in the context of a target repository. Thanks to an extensible integration interface, its architecture can be extended to define custom policies, suppression terms, and providers. Its interface also allows it to integrate with support platforms, build processes, and custom release systems.
Faraday
With Faraday, you can automate vulnerability management and control actions to put your attention on the work that really matters. Its workflows allow you to trigger any action with custom events that you can freely design to avoid the repetition of tasks. Faraday gives you the ability to standardize and integrate your security tools into your workflows, obtaining vulnerability information from more than 80 scanning tools. Using agents, the scanners are automatically integrated into your workflows to ingest and normalize data with maximum ease, generating results that can be viewed through a web interface. A remarkable and interesting aspect of Faraday is that it uses a centralized repository to store security information, which can be easily analyzed and tested by different members of the DevSecOps team. This brings an additional benefit, which is the ability to identify and combine duplicate issues reported by different tools. This reduces the efforts of the team members, avoiding them having to pay attention several times to the same issue that is reported more than once.
CircleCI
To integrate CircleCI with the most popular DevOps security tools, you must include one of its many partners in your development pipelines. CircleCI partners are solution providers in several categories, including SAST, DAST, static container analysis, policy enforcement, secrets management, and API security. If you need to do something to secure the development pipeline that you can’t do with any of the available orbs, you can take advantage of the fact that orbs are open source. For that reason, adding functionality to an existing orb is just a matter of getting approval for your PR and merging it. Even if you have a use case that you feel is outside the set of orbs available on the CircleCI registry, you can create one and contribute it to the community. The company publishes a list of best practices for creating automated orb compilation and testing pipelines to ease your way. To secure your pipeline, eliminate the need for in-house development and allow your team to leverage third-party services. By using CircleCI orbs, your team will only need to know how to use those services, with no need to learn how to integrate or manage them.
Trivy
Trivy is an open-source security tool that has multiple scanners capable of detecting security issues and various targets where it can find such issues. Among the targets that Trivy scans are: filesystem, container images, Git repositories, virtual machine images, Kubernetes, and AWS repositories. By scanning all of these possible targets, Trivy can find known vulnerabilities, configuration flaws, secrets or sensitive information, and software licenses and detect problems in the software supply chain, including dependencies on software in use and operating system packages. The platforms and applications with which Trivy can integrate can be found on its Ecosystem page. This list includes the most popular names, such as CircleCI, GitHub Actions, VS Code, Kubernetes, or JetBrains. Trivy is available in apt, yum, brew, and dockerhub. It has no prerequisites such as databases, deployment environments, or system libraries, and its first scan is estimated to be completed in just 10 seconds.
GitLeaks
Gitleaks is an open-source tool with a command-line interface that can be installed using Docker, Homebrew, or Go. It is also available as a binary executable for the most popular platforms and operating systems. You can also deploy it directly into your repo as a pre-commit hook or as a GitHub share via Gitleaks-Action. Its command interface is simple and minimalistic. It consists of just 5 commands to detect secrets in the code, protect secrets, generate scripts, get help or show the version of the tool. The detect command allows scanning repositories, files, and directories. It can be used on development machines as well as in CI environments. Most of the work with GitLeaks is done using the detect and protect commands. These operate on Git repositories, parsing the output of git log or git diff commands and generating patches that GitLeaks will then use to detect and protect secrets.
Stay Competitive and Secure
On the one hand, the agility and speed of your CI/CD pipelines are key to ensuring a fast time to market, which in turn is key to staying competitive as a software developer. On the other hand, including security tools in your development processes is an undisputed necessity. To incorporate security without negatively affecting your SDLC timelines, DevSecOps tools are the answer.